Published: February 25, 2025
Last modified: February 25, 2025
Yocto Project developers have used “cve-check” to check their builds for known vulnerabilities for years. While the tool has many advantages, the environment is changing, and we are working on a solution that will work for years to come.
Background
“cve-check” is built into the Yocto Project build flow and takes advantage of the metadata in the build system, including product names, versions, and even overrides (modifications of the automated scan results). The tool is also fast; the scan itself (when the database is up to date) adds a small one-digit number of minutes to a complete build.
However, the tool depends on the NVD database. The database experienced a slowdown in adding entries at the beginning of 2024 and hasn’t recovered since. During that time, the source data (the CVE database) added a way to include machine-readable product/vendor names, which was a blocking point for our use before.
In addition, new regulations (like the Cyber Resilience Act) require products to check for vulnerabilities and release updates for years of the product’s lifetime. Therefore, it is essential to generate scan results years after the original build. It would be better to be able to do that without having to keep the complete build directory, especially if we do not need all that information for the scan.
How to use?
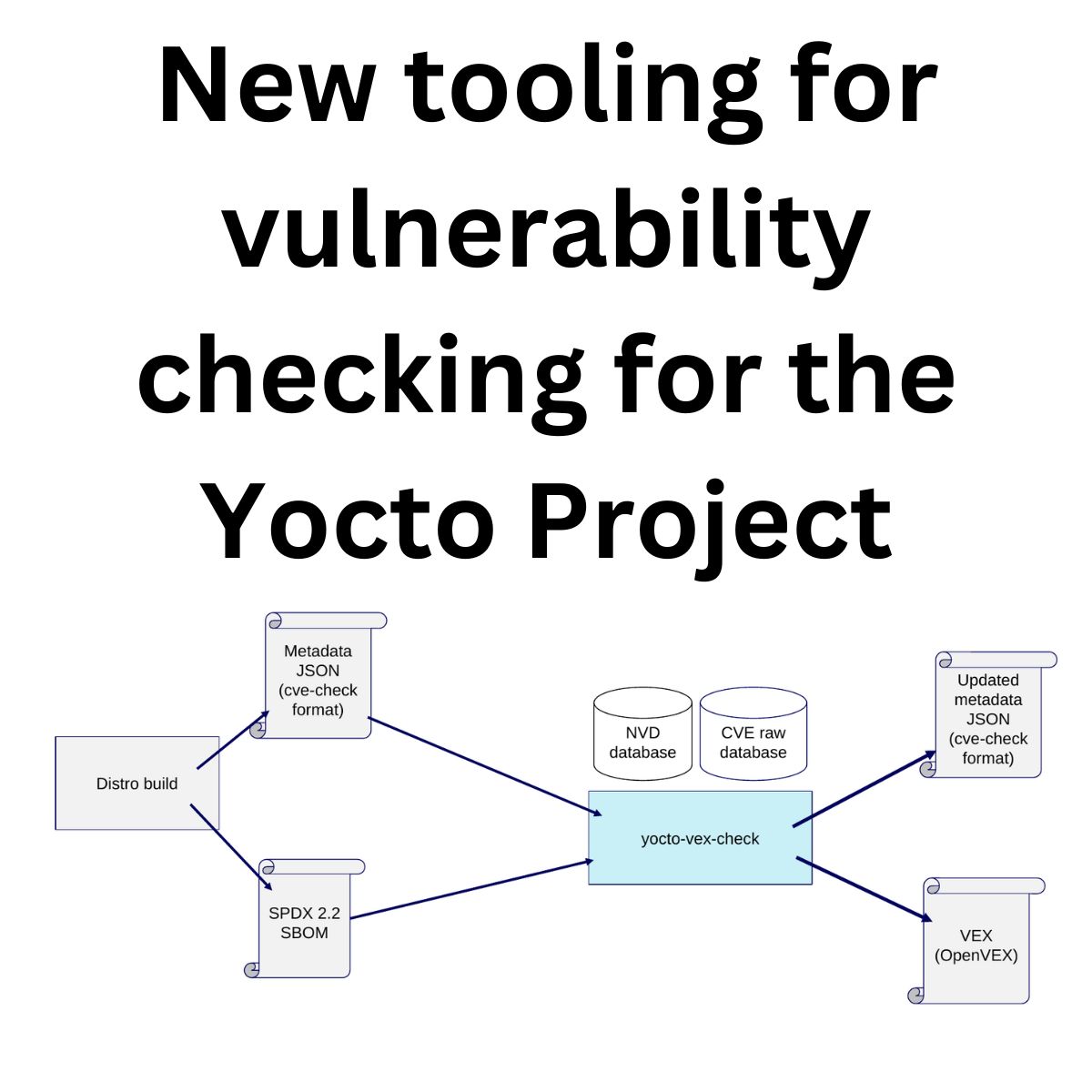
Because of all those reasons above, we created the yocto-vex-check, a tool that works on the metedata generated during the build, and can generate a complete vulnerability status up to date.
Clone the project’s repository from https://gitlab.com/syslinbit/public/yocto-vex-check
Download the database to use:
- for NVD, use cve-update-nvd2-native.py
- for the CVE database, get the CVEv5 git repository: either the upsteam one at https://github.com/CVEProject/cvelistV5 or the one with OE-related fixes at https://github.com/mrybczyn/cvelistV5-overrides (recommended)
Enable the vex class in your YP-based distribution build by adding to your local.conf:
INHERIT += "vex"Remove INHERIT += “cve-check”
Build your image as usual and note the location of the CVE JSON file (in the output of the build)
(Recommended for production builds) Archive the CVE JSON file and the SPDX archive
You are now ready to use yocto-vex check. The most common command looks like:
./wrap-yocto-vex-check.py \
-i ../openembedded-core/build/tmp/log/cve/cve-summary.json \
-o out-check-test \
-t temp-out-check \
-db ../cvelistV5-overrides/ -db-type CVEWhere:
-i gives the input metadata generated by your build and the vex.bbclass
-o is the output directory for the final status file and VEX files
-t is a temporary directory the tool needs
-db allows to select the database location
-db-type informs which database to use: CVE or NVD
The tool will work for a minute or two and output a file in your output directory, you can view it manually with cat or jq, or use our statistics script like:
./script/cve-report.py -s -i out-check-test/cve-summary.json
Issues for package linux-yocto (version 6.12.9):
Unpatched: CVE-2021-46978 CVE-2021-47089 CVE-2021-
47137 CVE-2024-26666 CVE-2024-34027 CVE-2024-35919
Count: 6
Global issue count: 6
#The tool is in active development we are looking for suggestions and reviews!
FAQ
Why not to use an existing tool?
Existing tool for vulnerability checking do not take into account the metadata included in the recipes of the Yocto Project. You can integrate such tools as checkers in the yocto-vex-check, however.
Do you plan to integrate this tool into the Yocto Project?
Yes, definitely, this is ongoing work.
Is this tool open source?
Of course!
Additional resources
We have presented the tool at FOSDEM 2025, you can see the slides below and view the video.
Presentation slides:
FOSDEM202502_Vulnerability-Reporting-at-Scalev3Presentation video: